Helps students (primarily incoming college freshmen) develop the foundational computing and information literacy skills that they will need to succeed in other courses.
Responsible Computing
$25
- Description
- What students will learn
- Learning objectives by module
- Course assessments, activities, and outline
- Other course details
- System requirements
- Included instructor tools
Description
Members of the Carnegie Mellon University (CMU) academic community have access to extensive computing resources. Like any community, CMU has certain rules and standards that set expectations of behavior. This course helps students better understand what the expectations are for responsibly using CMU’s computing resources, focusing on common problems that students have and areas that often cause trouble. It introduces students to some of the most commonly used technologies, tools, and resources, teaches them how to use them, and explains how to get help if they run into problems. Additionally, it teaches students their responsibilities for protecting information and computing resources by avoiding behavior that could lead to a compromise, as well as explaining online threats and risks, and the various ways to protect themselves. Lastly, it teaches students how to define what information they need for specific research purposes, locate the best sources, evaluate them, and use them in their work.
This course was specifically designed to be taught at CMU, but can be used in part or adapted by other institutions. At CMU the course is offered in a hybrid format, meaning that students work through the online course materials and then attend a weekly recitation session to further review concepts that were challenging and to get personalized help with any learning objectives that they couldn’t master on their own.
If you are interested in reviewing the course material to decide if it would be useful at your institution, please contact us.
Topics Covered:
Responsible Computing, Effective Computing, Safe Computing, and Information Literacy.
Suggested Prerequisites:
None.
Additional Software or Materials Required:
None.
What students will learn
By the end of this course, students will have a working knowledge of the rules and standards of CMU’s academic community, with regard to its computing assets. They will learn to:
- develop strong learning strategies for Responsible Computing and other online courses.
- recognize appropriate and inappropriate behavior with regard to use of CMU computing resources.
- identify risks to their personal information and resources.
- utilize academic spaces, software, and equipment appropriate to a variety of situations.
- locate and operate useful tools and resources on the University Libraries website.
- search effectively for information on the Web and in academic databases.
Learning objectives by module
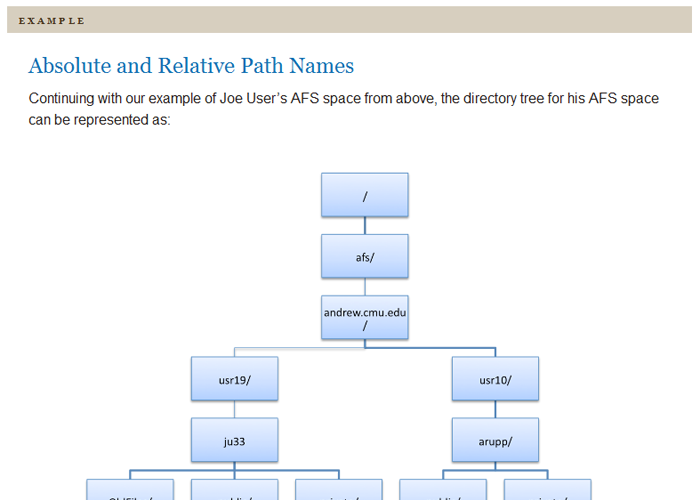
Unit 1: Computing@Carnegie Mellon
- Module 1: About Computing@Carnegie Mellon
- Identify the available support options.
- Recognize appropriate study strategies inparticular situations.
- Use the course resourcesto effectively support your learning.
Unit 2: Responsible Computing
- Module 2: Introduction to Responsible Computing
- Describe specific risks to the CIA of university resources that result from common student behaviors.
- Identify appropriate (and inappropriate) use of sharing digital content, and recognize some of the most common consequences of misuse.
- Identify risks to your personal information and resources along the dimensions of confidentiality, integrity, and availability (CIA).
- Recognize inappropriate behavior with regard to the use of computing resources.
- Summarize your privileges and responsibilities as a member of the Carnegie Mellon community.
- Module 3: Privileges and Responsibilities
- Define quota as a rationing of shared resources and identifyresources to which a quota may apply.
- Describe the range of penalties for misuse of computingresources.
- Recognize inappropriate behavior with regard to the use ofcomputing resources.
- Summarize your privilegesand responsibilities as a member of the Carnegie Mellon community.
- Module 4: Protecting Information and Resources
- Describe specific risks to theCIA of university resources that result from common student behaviors.
- Identify practices forprotecting the CIA of your personal information.
- Identify risks to your personalinformation and resources along the dimensions of confidentiality, integrity andavailability (CIA).
- Predict the impact of specificactivities on the confidentiality, integrity and availability of personal and universityresources and recommend appropriate actions based on those predictions.
- Recognize personal information thatis protected by your Andrew ID and password.
- Module 5: Copyright and Digital File Sharing
- Define P2P and identify the risksinvolved in using file-sharing technology.
- Describe the penalties forbeing the target of a DMCA Takedown Notice.
- Identify appropriate (andinappropriate) use of sharing digital content, and recognize some of the most commonconsequences of misuse.
- Summarize your and the university’sobligations under the DMCA (Digital Millennium Copyright Act).
Unit 3: Effective Computing
- Module 6: Introduction to Effective Computing
- Explain how the Andrew Printing quota system works and how to monitor your usage.
- Identify the features that you should consider when selecting a file storage and sharing space.
- Identify the options for getting help and the process for reporting problems.
- Locate academic spaces, software, and equipment and select an appropriate resource to use in a given scenario.
- Select an appropriate Andrew print queue for common print jobs and print from a computer lab or personal computer.
- Select an appropriate file storage space from those offered by Carnegie Mellon.
- Module 7: Academic Spaces, Software and Equipment
- Locate academic spaces, software and equipment.
- Select an appropriate resource in a given scenario.
- Module 8: File Storage and Sharing
- Identify the features that youshould consider when selecting a file storage and sharing space.
- Save and open files fromCarnegie Mellon’s file storage spaces.
- Select an appropriate file storage space from those offeredby Carnegie Mellon.
- Share files with other CarnegieMellon users.
- Use strategies fordetermining the best storage option in a given scenario.
- Module 9: Andrew Printing
- Explain how the Andrew Printingquota system works and how to monitor your usage.
- Locate resources to configureyour personal computer for an Andrew Printing queue.
- Print to an Andrew print queue from a computer lab orpersonal computer.
- Select an appropriate print queuefor common print jobs.
- Module 10: Getting Help and Reporting Problems
- Identify the options for getting help andthe process for reporting problems.
Unit 4: Safe Computing
- Module 11: Introduction to Safe Computing
- Appropriately select preventative tools and security practices to protect personal and university computing assets, and recognize and apply appropriate steps if you become the victim of an electronic attack.
- Identify security risks and ways to protect yourself against them.
- Identify the aspects of your online presence that are most susceptible to risk or compromise, and recognize the consequences of a compromise.
- Module 12: Your Life Online
- Identify aspects of your online presence that are mostsusceptible to compromise and the associated consequences of a compromise.
- Module 13: Security Risks
- Identify security risks and apply appropriate measures to protect yourself.
- Module 14: Protection from Malicious Attacks
- Describe the steps you should take to recover from amalicious attack.
- Identify aspects of your online presence that are mostsusceptible to compromise and the associated consequences of a compromise.
- Identify malicious attacks and apply appropriatemeasures to protect yourself.
- Identify resources the university provides for securitynews and alerts.
- Identify ways to protect your mobile devices fromsecurity risks and malicious attacks.
Unit 5: Information Literacy
- Module 15: Introduction to Information Literacy
- Critically evaluate sources.
- Distinguish differences in the structure of the Web and academic databases, and identify effective ways to use each.
- Identify reasons, contexts, and formats for appropriately citing sources.
- Locate and operate useful tools and resources on the University Libraries website.
- Search effectively for information on the Web and in academic databases.
- Module 16: Navigating the Library Website
- Locate and operate Course Reserves.
- Locate and operate Interlibrary Loan.
- Locate and operate My Account.
- Locate and operate the Ask Us feature for getting help.
- Locate and operate the library catalog (CAMEO), databases, and e-Journals.
- Locate and operate useful tools and resources on theUniversity Libraries website.
- Operate EZproxy to access library resources.
- Module 17: Understanding Information
- Construct simple research strategies for using Internetsearch engines and academic databases appropriately.
- Identify appropriate uses for Internet search engines andacademic databases.
- Identify basic differences between Internet search enginesand academic databases.
- Module 18: Effective Searching
- Determine whether full-text resources areavailable and find them if they are.
- Find information using CAMEO,general and specialized databases, and the Web.
- Generate appropriate search strategies forparticular stages of the research process.
- Generate appropriate search terms for differentkinds of search engines.
- Revise searches effectively by changing searchterms, using facets, adding key words, and employing advanced searchoptions.
- Module 19: Evaluating Sources
- Identify four criteria for evaluating sources:currency, relevance, point of view and authority.
- Use the criteria of currency, relevance, point ofview and authority to evaluate sources in relation to particular research goals andobjectives.
- Module 20: Academic Integrity
- Distinguish legitimate from illegitimateparaphrasing.
- Identify best practices for avoiding situations that might lead to academic integrity violations.
- Identify reasons why integrity matters in youracademic work.
- Identify the range of consequences for academic integrity violations.
- Identify ways to maintain integrity in youracademic work.
- Recognize instances of academic dishonesty.
- Recognize the types of sources you must cite and create appropriate citations.
Course assessments, activities, and outline
UNIT 1: Responsible Computing
Module 1: About Responsible Computing
UNIT 2: Responsible Computing
Module 2: Introduction to Responsible Computing
Pre-Assessment: Responsible Computing
Module 3: Privileges and Responsibilities
Module 4: Protecting Information and Resources
Module 5: Copyright and Digital File Sharing
Exam-Readiness Quiz: Responsible Computing
UNIT 3: Effective Computing
Module 6: Introduction to Effective Computing
Pre-Assessment: Effective Computing
Module 7: Academic Spaces, Software and Equipment
Module 8: File Storage and Sharing
Module 9: Andrew Printing
Module 10: Getting Help and Reporting Problems
Exam-Readiness Quiz: Effective Computing
UNIT 4: Safe Computing
Module 11: Introduction to Safe Computing
Pre-Assessment: Safe Computing
Module 12: Your Life Online
Module 13: Security Risks
Module 14: Protection from Malicious Attacks
Exam-Readiness Quiz: Safe Computing
UNIT 5: Information Literacy
Module 15: Introduction to Information Literacy
Pre-Assessment: Information Literacy
Module 16: Navigating the Library Website
Module 17: Understanding Information
Module 18: Effective Searching
Module 19: Evaluating Sources
Module 20: Academic Integrity
Exam-Readiness Quiz: Information Literacy
UNIT 6: The Final Exam
Responsible Computing Final Exam
UNIT 7: Back-Up Final Exam
Responsible Computing Final Exam
Other course details
System requirements
OLI system requirements, regardless of course:
- internet access
- an operating system that supports the latest browser update
- the latest browser update (Chrome recommended; Firefox, Safari supported; Edge and Internet Explorer are supported but not recommended)
- pop-ups enabled
- cookies enabled
Some courses include exercises with exceptions to these requirements, such as technology that cannot be used on mobile devices.
This course’s system requirements:
- none listed (subject to change)
Included instructor tools
Instructors who teach with OLI courses benefit from a suite of free tools, technologies, and pedagogical approaches. Together they equip teachers with insights into real-time student learning states; they provide more effective instruction in less time; and they’ve been proven to boost student success.